We are witnessing the collapse of the "Trust Me" era of cloud computing.
For the last decade, we have operated on a presumption of benevolence. We hand our data and our logic to a cloud provider, and we trust that the admin won't peek, the hypervisor won't tamper, and the logs won't be wiped. When AI was just generating poems, this risk was manageable.
Now that AI is becoming agentic — moving money, executing contracts, and managing critical infrastructure — the "Trust Me" model is an existential liability. You cannot build a billion-dollar autonomous workforce on a foundation of "please don't be evil." You need a guarantee that the agent can’t be evil.
This is the Hardware Renaissance.
In my latest preprint, published today on Zenodo, I map the emerging ecosystem of Trusted Execution Environments (TEEs). While the underlying silicon is often shared (Intel SGX, TDX, NVIDIA H100), the architectures built on top of them are solving radically different problems.
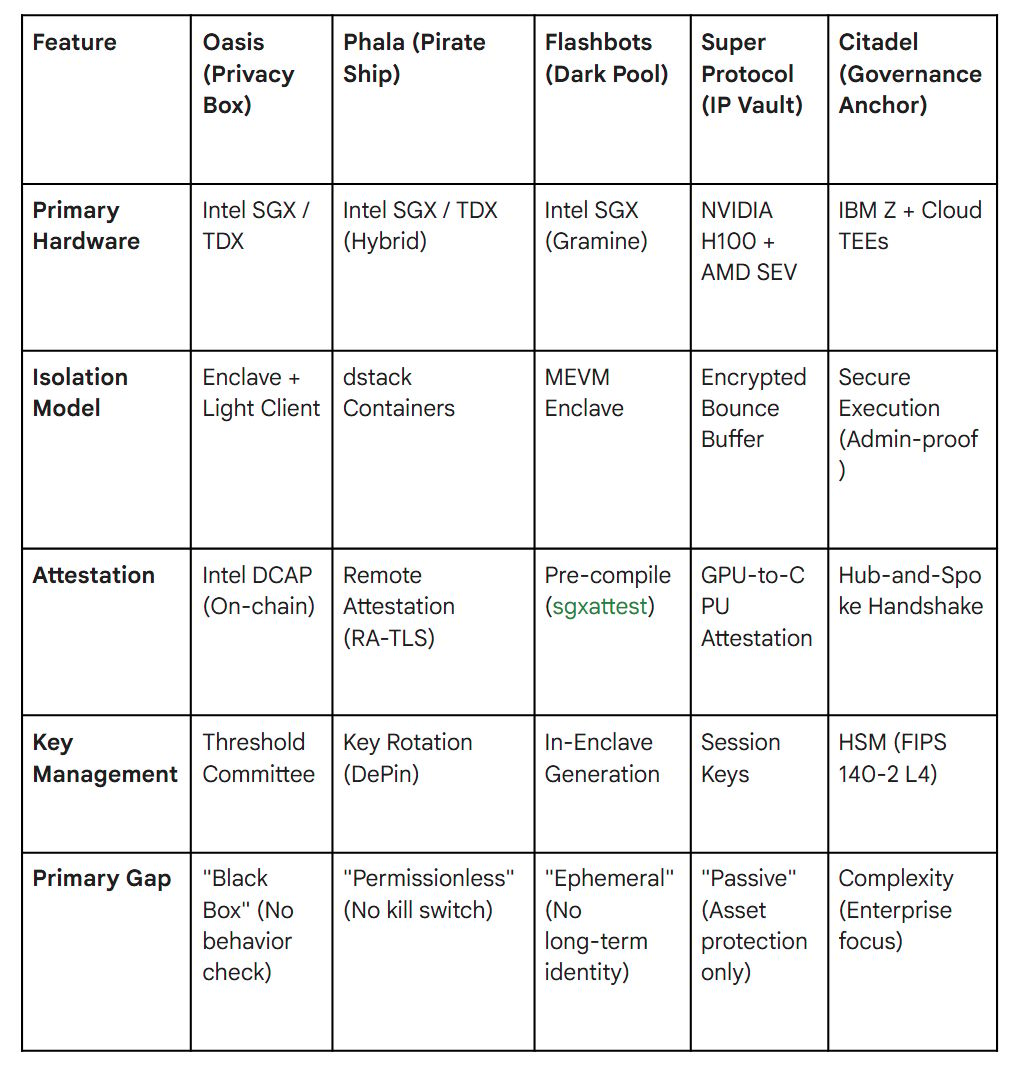
I have categorized the market into five distinct archetypes to help architects match their threat model to the right infrastructure:
The Privacy Box (Oasis Network) — For when you need to hide the state of a dApp from the public chain.
The Pirate Ship (Phala Network) — For when you need unstoppable, censorship-resistant agents that operate outside the reach of any central kill switch.
The Dark Pool (Flashbots SUAVE) — For when you need to solve the physics of transaction ordering and MEV without exposing user intent.
The IP Vault (Super Protocol) — For when the "crown jewels" are the model weights themselves, and you need to protect them from the cloud provider.
The Governance Anchor (The Citadel Protocol) — For when you need strict, regulatory compliance (ISO 42001) and an immutable audit trail for enterprise risk management.
This paper is a technical deep dive into the attestation flows, memory isolation, and key management strategies that define these architectures. It is an attempt to bring clarity to a confusing, fragmented, and critical layer of the new AI stack.
If you are building agents, you need to understand the ground you are building on.
Read the full paper on Zenodo: The Hardware Truth Landscape — Pirates, Traders, and Anchors